To start, he highlights the critical role of AI in safeguarding the future of cloud security. Particularly he mentions the outdated reliance on passwords, and embraces a new era of AI-driven protection.
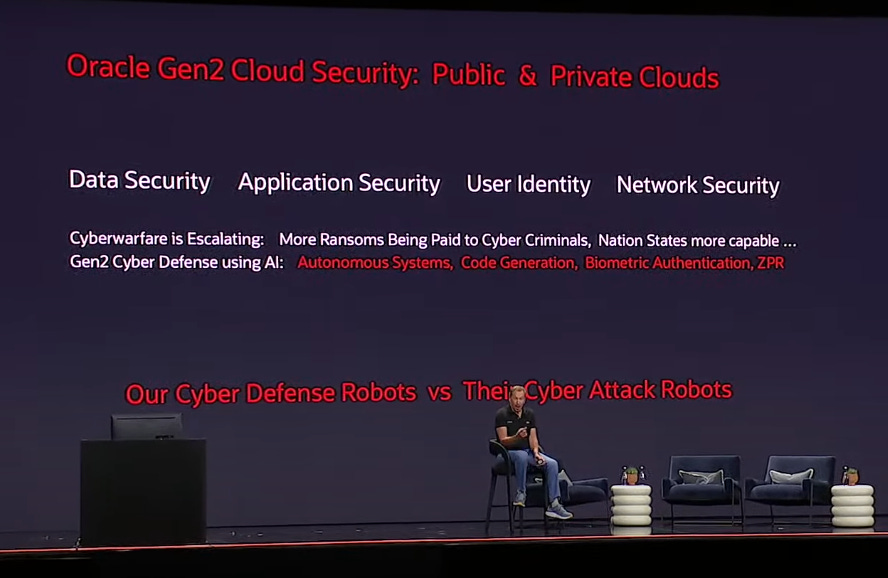
There are four key pillars of AI-powered security:
Data Security: Oracle advocates for fully autonomous database systems, eliminating human error, the primary cause of data breaches. The Oracle Autonomous Database, with its robotic DBA, automates tasks like configuration, encryption, backups, and patching, ensuring data integrity and minimizing vulnerability.
Application Security: Oracle's APEX code generator utilizes AI to create secure and reliable applications, eliminating security vulnerabilities and ensuring automatic recovery in case of failures. This approach delivers significant productivity gains while enhancing security.
User Identity: Ellison argues for the replacement of passwords with biometric authentication, using facial recognition, fingerprint scanning, and voice recognition to verify identity, creating a more secure and user-friendly experience.
Network Security: Oracle introduces ZPR, a next-generation network security system that separates security from configuration. ZPR utilizes AI-powered robots to inspect network packets, ensuring only authorized data transfers and preventing malicious data exfiltration.
Ellison's vision for the future of cloud security relies heavily on AI-driven automation. By automating data security, application development, user authentication, and network protection, Oracle aims to significantly enhance security while minimizing human error and creating more efficient operations.
Summaries:
Passwords are dangerous, so all Oracle will drop in 2025. Optional for customers.
Biometric user identity to combat fraud and identity thefts in health & finance.
Database autonomy for configuration, encryption, updates, and backup.
Human error are avoidable by Code Generation with APEX for English prompts.
Zero Trust Packet routing focused on policy to fix network security complexity.
Virtualization with separating routes to isolate from the public internet.
Mitigation with Oracle defend robots vs. attack robots with Gen2 Cyber Defense.
Full Video ( Start from 35:00-)
Full script:
“Oracle can use AI to dramatically improve cloud security – improve it by a factor of 10 or a factor of 100, do things that everyone wants, like getting rid of passwords. Passwords are a terrible idea. Passwords that are 17 characters long, including special characters that no one can ever remember and has to write down, are unbelievably easy to steal. The cyber wars are getting worse, not better. The industry has got to find better ways to authenticate people than asking them to type in a password.
There are four pillars of security at Oracle.
One is data security. Make sure that, under no circumstance, can people look at your data, steal your data, or lock you out and away from your own data. Oracle has to absolutely have absolute data security. Everyone knows Oracle's first customer was the Central Intelligence Agency, and they take data security very seriously. Oracle has taken data security very seriously since they started the company. He thinks they're pretty good at keeping your data safe but is going to talk about more things that they are doing to keep your data safe.
The next is application security. Oracle writes a lot of applications. They wrote NetSuite, Oracle ERP, Oracle HCM, Oracle Fusion CX, all of those applications. How do they write those applications so that they're more secure than they are now? Do they just do a better job of training their programmers? Do they make sure they audit all the code to make sure there are no security vulnerabilities? What do they do?
Next is user identity. He said passwords. Got to get rid of them.
And then finally, network security. How do they make sure that a bunch of credit card data isn't flowing from one of their databases onto the internet, data is not being exfiltrated? How do they continuously monitor their network to make sure no data is flowing from point A to point B where point A and point B are not pre-authorized by your security system?
What is needed is a set of cyber robots, defense robots, to stop these attacks.
Data security (Autonomous Systems)
How do they keep your data safe? Very simply, using Autonomous systems.
Autonomous, fully automated, fully self-driving systems. Just like self-driving cars. Self-driving cars are much safer than human-driving cars. The robot isn't going to go 130 miles an hour on the freeway. The robot is not going to have a few drinks after dinner and get in the car. They can save lots of lives with autonomous driving cars. They can do a better job of protecting data if the database system that is managing that data is fully autonomous. And this is something that Oracle has been working on for a very long time, and they think they're quite good at it. Almost all cyberattacks begin the same way: with human error.
The Oracle Autonomous Database has a robot DBA. The robot DBA automates everything. Human beings don't configure the database.
There's a famous story of a large bank running a big application in a cloud that lost all of their credit card data. And it came out that the bank's programmers made a mistake configuring the system, configuring the database, and they left it vulnerable to the public internet. And literally every single credit card user lost their credit card data.
That cannot happen with the Oracle Autonomous Database because human beings do not configure the system.
Robots configure the system. It is fully self-driving. It configures itself.
It encrypts everything. It backs itself up. If you have to recover from a backup, it does that fully automatically.
There are no human beings involved in backup; there's no human being involved in recovery.
A new version of Oracle comes out. The software automatically gets updated. There's a security patch that's available. It automatically patches itself. You need more capacity. Well, because they use a cluster, the database runs on clusters, Exadata clusters, and Exascale. The next generation of Exadata called Exascale runs on Exascale clusters.
If you need more processors, they just get them from the pool. But it's done automatically. Human beings don't do that. If a bunch of processors go down, the system keeps running. Who keeps it running? It does that automatically. There are no human beings involved.
If the data center catches fire and burns to the ground, your application is running in a separate data center without missing a beat. No human beings involved in the recovery whatsoever. No human labor, no human error.
But you have to be willing to pay less to use Autonomous systems. It's interesting that it is the most economical way to do things and the safest way to do things.
This is so important to Oracle that they have decided that all of their applications have to be moved to the Oracle Autonomous Database because it is so much more secure than a database where you have DBAs configuring the system. DBAs backing up the system, recovering the system. So already, a lot of Oracle stuff runs on autonomous.
The new Cerner Health system called New Millennium runs on the Autonomous Database. They're building next-generation fusion sales and fusion marketing. New products in fusion sales and fusion marketing. They're not obsoleting anything from fusion. But the new updated versions of fusion sales and marketing run on the autonomous database. Almost all of the industry applications run on the autonomous database. It's more secure, it's much more reliable, it's much less expensive to use.
And by 2025, they will have moved all of their applications to the autonomous database. They will be off the older databases. Everything must be autonomous.
Not to save money, but to keep the data safer, to have no human labor, no human error. So that's the first thing. The first thing they do for security is using AI to build autonomous systems and get rid of human errors that allow people to steal your data.
Another thing that runs on the autonomous database is the Oracle Cloud.
There are lots of things in the Oracle Cloud. They keep track of your configurations; they keep track of user authentications and all of those things. All of the databases that run the Oracle Cloud must be autonomous. They can't have their cloud at risk. It's got to be autonomous.
And right now, almost every database in the Oracle Cloud is autonomous. He thinks there might be a couple of exceptions, but pretty much all of it has been migrated to autonomous. It makes OCI faster and much more reliable and requires much less human labor. It allows all of their data – the idea is that all of their data centers need to be automated.
All of their data centers need to be fully automated. If they're going to provide you with the economies of a low-cost, high-performance cloud, they have to be able to keep it secure and minimize labor.
Application security: Code generation
The next pillar of security, using AI again, people talk a lot about code generation. Everyone's very excited that ChatGPT can write Java. It can. It can write Python; it can write JavaScript; it can write a whole bunch of things. It's very interesting. Some code generation uses a large language model to generate a traditional familiar language like Java.
But you can also build code generators specifically to generate applications. When you use a large language model to generate applications, you translate English into Java.
And some people think that might not be the most efficient way to describe programs in the English language. Everyone knows the English language. Everyone in this room probably knows the English language, but it might not be the most precise way to describe a computer program.
Both types of code generation are useful, where you invent a new language that's designed to be a code generator and it builds the application, or you use English, describe it in English, and build the application from English. This is an area where Oracle has built a language called APEX and made, in the last couple of years, since the dawn of the AI era, huge changes to APEX.
And it can now generate very sophisticated applications. And when it generates the application, it's very interesting. By the way, they're generating the majority of the new applications that they're "writing." They're not writing them; they're generating them using APEX. Oracle is both an infrastructure company and an application company, and more and more of their applications are generated using APEX.
So what are some of the advantages of using APEX? It has 10x productivity versus hand programming in Java. It gets huge productivity gains. More important is the security. When the application generator generates the code, it doesn't generate security vulnerabilities.
A computer program is writing the code. It will not make that mistake. It will not generate a vulnerability that you have to fix later on. It will not create something called state in an application.
There are stateful applications and stateless applications. A stateless application, if your data center burns down, can be immediately failed over to a different data center. They're easy to recover, but you have to make sure you write the program properly, and it has to be stateless to make it fully recoverable.
The generated applications are more secure because they don't generate security vulnerabilities, and they're more reliable because if a power line should be cut to your data center for whatever reason and you lose power, you can immediately failover to a different computer in that data center or in a different data center because the application was generated to be fully recoverable, a stateless, fully recoverable application.
Oracle generates more secure, more scalable, stateless, recoverable applications, and they get a 10 times productivity gain to go along with it. Apex is the vast majority of new applications that are being started today are being written in a code generator, not a traditional programming language, because it's more productive and secure.
User Identity: Biometric Authentication
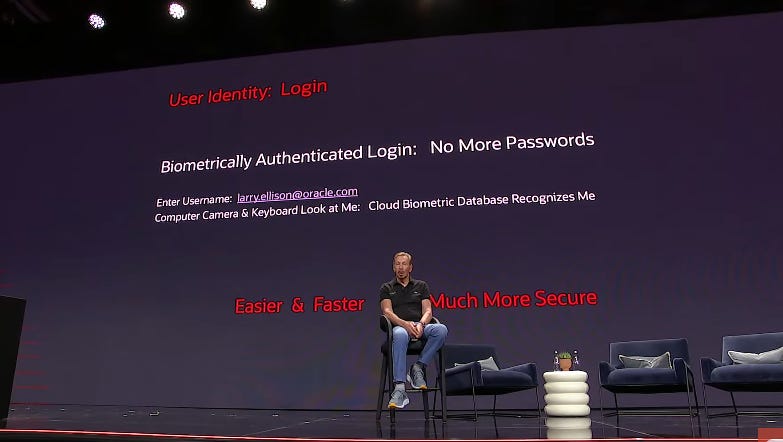
The third pillar of using AI to make your systems more secure is user identity. This one, is, in some ways, the most obvious. Everyone is going to be very excited about it. When you log into a computer, why do you type in a password? His name is larry.ellison@oracle.com. That's who he is in cyberspace. He's larry.ellison@oracle.com.
Now, why do you want him to type in a password? When he sees Safra, she doesn't ask him for his password. And she recognizes him.
A computer can't do that? Of course, a computer can do that. A computer can look at you; the camera can look at you.
If you put your index finger on the Return key, a camera can recognize you from your index fingerprint; it can recognize your face; it can recognize your voice.
Why do you want a password? What is the purpose of this thing? People can't imitate your fingerprint; they can't imitate your face; that's very hard to do. So type in who you are, and they'll automatically authenticate you from a biometric database in the cloud. That's simple. They know who you are, and they recognize you. People in the audience are probably saying, "Why do I have to type in larry.ellison@oracle.com? Why can't you just recognize me?" They can do that, too. You don't have to type that in either.
But the idea that we use passwords is a ridiculous idea. It's obsolete. It's very dangerous. Passwords are collected. Now that they've made passwords very hard to remember, people write them down. And then they use the same password, the same exact password in every single logon, every e-commerce logon they have. They reuse the same password over and over again. And then those passwords get stolen and resold on the dark web, et cetera.
Biometric logins are much easier to use, much faster, and much more secure. It takes a couple of minutes to register yourself biometrically in a biometric database. You point your smartphone at your face for a couple of seconds, you put your fingerprint on the smartphone, you can record your voice if you want to, and it registers in a biometric database, the login database, in a couple of minutes.
By the way, a year from now, you won't be able to log in to Oracle using passwords. They are just not secure. Therefore, that option is going to be gone inside of Oracle. Not everyone needs to do this; it's 100% voluntary, but it is much, much more secure.
And there are lots of applications for biometric authentication. He's had to cancel credit cards, and other people stole his credit card number. People walk into stores, impersonate him, all of this stuff. They cancel his credit card.
But identity theft is very common. They can have biometrically authenticated credit cards, the same exact system. And people seem to like biometrically authenticated credit cards.
Apple Pay is an example; Google Pay is an example. But they think rather than keeping the authentication in your smartphone, you have to have your smartphone with you all the time, though people carry it all the time. It's better and more secure and safer to keep it in a biometric database. And they can authenticate about 22,000 credit card transactions per second in the world. They can very easily authenticate them within subsecond response time, authenticate people at a rate of 22,000 per second or much higher. That is not really a problem; they can do that. It's got to be up 7 days a week, 24 hours a day, and can never go down.
Well, that's how they built the Oracle Database. Because it runs on cluster hardware, it is fully fault-tolerant; they don't ever have to go down. They live patch the database typically. They don't go down. So they can do this. They can make it so much easier. They can deliver absolutely fraud-proof credit cards that are biometrically authenticated. And there are many other applications.
Passport control – a lot of people, when you land at the airport, and you're on the speed line going through, are getting biometrically authenticated. The camera's looking at your picture and saying, OK, you are Larry Ellison. You just walk through. But what about schools? How do they make sure there's no one on campus that is not authorized to be there? They can use biometrics to make sure that there is no one entering the school building that shouldn't be entering the school building. There's no one driving into the parking lot who's not allowed to drive into the parking lot. They look at license plate readers and facial recognition, pick up prescriptions.
There was massive fraud during COVID-19, people getting government entitlements for COVID-19 because they pretended to be 30 different people and collected 30 times more than they were supposed to. They can stop all of that. That's actually fairly easy to stop with biometric authentication. It becomes very difficult to impersonate somebody else if you have proper user authentication.
Network Security: Zero Trust Packet Routing
The last one, the fourth pillar, is network security. For network security, his dear friend by the name of Danny Hillis, the same guy who invented thinking machines when he was an undergraduate at MIT, came to Oracle with this idea called ZPR, which is a next-generation network security technology. And they worked with Danny, and they actually ended up buying a bunch of his company. And they took the ideas, Danny's ideas, and they implemented a new generation of network security. And it solves an incredibly important problem.
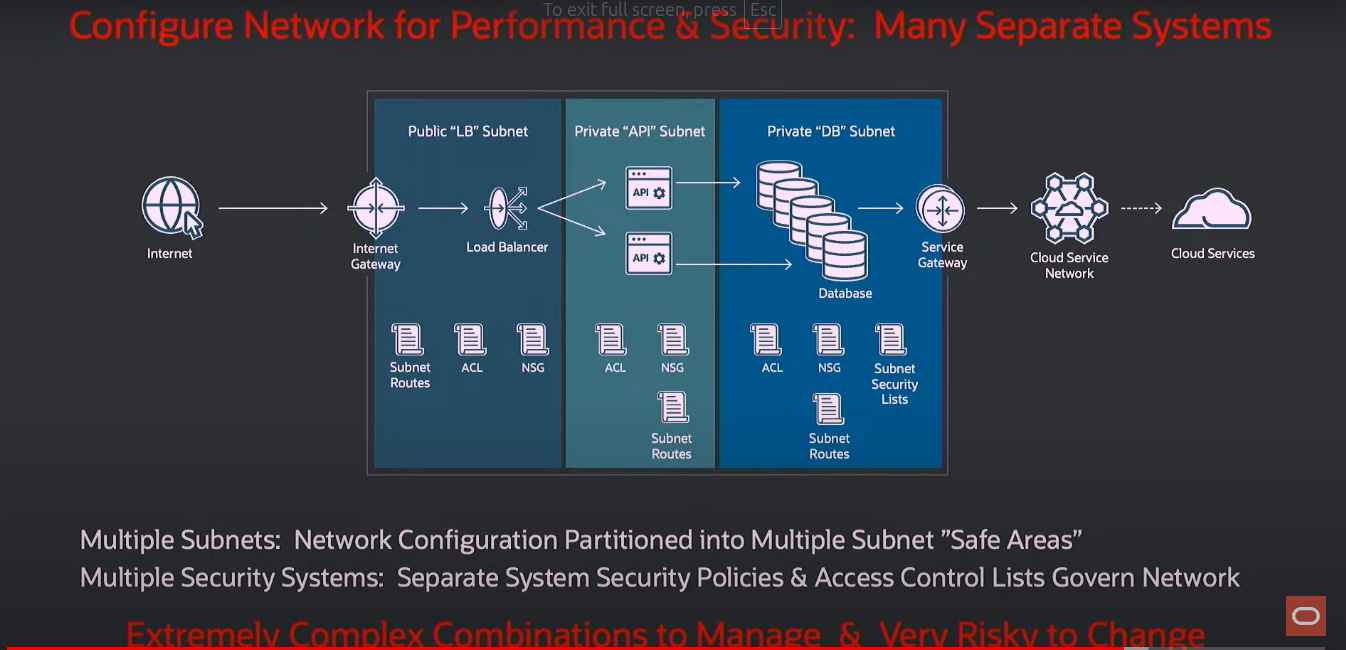
Network security: If anyone in the audience is in charge of securing the network, either on-premise or in a cloud, this is an astoundingly complicated problem. It's a very complicated problem because when you configure a network, there are two competing goals.
One is that you want to make it very high performance, very reliable, lots of pathways, a lot of bandwidth. You got to make it very fast. Everyone wants their network to be fast and reliable. And then they say, "By the way, while you're making it fast and reliable, I also want you to make sure that no one's on the network moving data from point A to point B where that is not allowed." They're going to give you this one set of tools to configure the network, but make sure two things are true: it's fast, and it's secure.
When you do that, and let's say you're trying to improve the performance of your network, you add ports or add routes. If you're not careful as you add ports and add routes and subnets and things like that, you could accidentally be creating these security vulnerabilities. It happens all the time.
It's why it's so difficult to get someone to change their network configuration because there are so many security audits required before you change your network configuration. And you get these unbelievably complicated pictures.
Over on the left, you've got the public internet. It's going through an internet gateway. It's going to a load balancer, a couple of load balancers, from load balancers to application servers, from application servers to database servers, from database servers through a cloud services gateway. It's an incredibly complicated picture. You try to configure the network with these separate zones, these safe areas called subnets. And it's very, very difficult to do. The slightest mistake can expose your data to the public internet, expose your data to hackers.
So the solution to the problem is that you really have to separate network security from network configuration. Network configuration – don't worry about two things; worry about one thing. Worry about making it fast and reliable. Then they'll build an all-new system that's responsible for network security.
And that all-new system will authorize certain paths through the network for certain users to use certain services, look at certain data, and only authorized paths are allowed, and no other paths will be allowed. It's a brand new network security system that is separate from network configuration rather than blended with network configuration.
And once again, they're going to use code generation. They're not going to have you write the code; they're going to have you simply specify the intent of how ZPR works.
And to enforce ZPR, they have a code generator. To enforce ZPR, they have computers in their cloud that will look at every single packet that goes through the network and makes sure it's an authorized journey from point A to point B. And that means they have these robots, inspecting packets in their network. Billions of packets are being inspected every second.
A simple example: The code generator authorizes the path, how it authorizes the data path. You simply say, "I'm having trouble." OK, there we go. [Larry points to the screen for the presentation] This is saying allow the accounting application to connect to the database, the accounting database. It says, "You've got a computer that is running the accounting applications, and it's allowed to talk to the accounting database." It might be the only application that's allowed to talk to the accounting database. And it's easy-to-read English.
So let's say they move the database from one location to another. They even expose it to the public internet. Well, the only thing that can access that database, according to ZPR, is the accounting application. You can move it wherever you want to. You will not be exposed by changing the configuration. You will not be exposing your data. That's a very big deal. The system robotic will automatically adapt. You can change your configuration; you can add ports; you can do all sorts of things, and ZPR will automatically regenerate new robots to make sure that your data is still protected.
And you get a much simpler network configuration. There are none of these subnets – you don't have to worry about security when you're configuring your network. You just worry about performance and reliability.
And to protect this network, the entire thing, the entire security program, is those four lines sitting in front of you.
And all of your security for your network is in one place. It's unified. It's all stored in one place, in one database, in the ZPR language. And the ZPR language then generates these robots. If the configuration changes, it knows the configuration has changed. It updates those robots immediately before the network is then available to use.
Oracle Cloud Infrastructure: Gen2Network + ZPR
They were able to implement ZPR in OCI because OCI has a very different network than any other cloud company. OCI has a Gen2 cloud with a Gen2 network. Their network architecture has different hardware and different software than any of the other clouds.
They have a network called RoCE, that's RDMA over converged ethernet. What is it? It's an unbelievably fast version of Ethernet with this thing called RDMA, which allows one computer to look into the memory of another computer it's connected to without going through the operating system. It's a very fast path that the computers can look at each other's memory if they're authorized to do that. So it's a super fast network, many times faster than typical networks. They also have network processors that isolate their computers, their network.
The Oracle Cloud network is isolated from the public internet, it's isolated from the internet period because they do all of their network routing and their own computers in their own network processors inside of their own hardware. They do that virtualization. They have that additional hardware in their computers, in their cloud, that does all of the network routing and does all of the network security. And then they have network controllers that just manage the network processors.
When Danny came along with his idea for ZPR, it fit perfectly into Oracle's Gen2 network architecture. So after a few discussions, they decided this is an ideal approach for the Oracle Cloud because they can do the packet inspection.
They have all of these network processors that can run these packet inspecting robots and run them very fast, easily do billions per second. It's not a problem because they have this smart network with these separate processors, separate memory that can do all of this packet inspection and make sure that only authorized routes, only routes that you authorized in the ZPR language, will propagate to make sure no one can exfiltrate, no one can take credit card data or Social Security card data and move it from point A to point B because it's not authorized.
Combining biometric identity, getting rid of passwords and using biometrics, with this new generation of ZPR, this code generator and these autonomous robots that do this packet inspection in the network, stops most serious cyberattacks.
It's almost impossible for users to infiltrate the system if you're protecting yourself using biometric authentication, and it's pretty much impossible to move data out of the system across an unauthorized route if it's not authorized explicitly by you. You have to explicitly say it's OK to move data from point A to point B.
If you don't say that, the packet inspection, the packet robots, the ZPR robots won't let the data move. And that's the vast majority of cyber attacks that they can block using the combination of ZPR and biometric authentication.
It's available in the Oracle Cloud as of today. They have implemented version 1 of ZPR in the Oracle Cloud today. By this time next year, Oracle employees won't be using passwords.
A lot of you will have the choice to not use passwords anymore but instead to use biometric identity, ZPR running, biometric identity, code generation from ZPR, code generation from APEX, Autonomous Database running on Autonomous Linux.
All of these AI technologies give the industry a chance to win the cyber wars. If you're worried about cybercriminals, and you think they pose a threat, wait till you look at the capabilities of nation states who can shut down utilities, entire utilities, in an unfriendly moment.
They need to make sure that our digital systems, our digital infrastructure, is much more secure than it is today, and they have the technology to do it.”